I always liked science fiction. Sometimes you are not sure where science ends and fiction begins. Graphene is much simpler.
Monday, October 25, 2010
A Parable for the 21st Century
Graphene as a Metaphor for God
1930’s Dictum: No large scale order can exist. The only way nature improves things is by survival of the fittest. The world’s greatest mathematicians and scientists, the weak and helpless alike are murdered in concentration camps. People die by the hundreds of millions in war and unspeakable atrocities. The theory was that graphene would collapse into a ball as with theories of the big bang, black holes, Evolution of the Species and other essentially unverifiable things. Chemists forbidden to say graphene can exist in free form. Almost like say being forbidden to say God exits and to deny the really of the observable universe, endorsing murder and all that is evil.
2004: Graphene, the first of similar materials, is found to exist. Now, one can imagine a universe made out of graphene without big bang, etc. with ferromagnetism by bending the graphene; directed gravity by spinning a ferromagnetic disk; BECs with double layer graphene. Transistors made out of graphene can function as frequency multipliers. Spintronics devices are possible. Valleytronics devices are possible. Graphene can be used to clean up oil spills and other pollutants. Supersensitive chemical detectors allow us to avoid hazards or map our genomes or epigenomes. Super strong one atom thick membranes can be used as touch screens or building anything you need. Everything that one needs to make Earth a paradise for all mankind is available by the grace of God.
1930’s Dictum: No large scale order can exist. The only way nature improves things is by survival of the fittest. The world’s greatest mathematicians and scientists, the weak and helpless alike are murdered in concentration camps. People die by the hundreds of millions in war and unspeakable atrocities. The theory was that graphene would collapse into a ball as with theories of the big bang, black holes, Evolution of the Species and other essentially unverifiable things. Chemists forbidden to say graphene can exist in free form. Almost like say being forbidden to say God exits and to deny the really of the observable universe, endorsing murder and all that is evil.
2004: Graphene, the first of similar materials, is found to exist. Now, one can imagine a universe made out of graphene without big bang, etc. with ferromagnetism by bending the graphene; directed gravity by spinning a ferromagnetic disk; BECs with double layer graphene. Transistors made out of graphene can function as frequency multipliers. Spintronics devices are possible. Valleytronics devices are possible. Graphene can be used to clean up oil spills and other pollutants. Supersensitive chemical detectors allow us to avoid hazards or map our genomes or epigenomes. Super strong one atom thick membranes can be used as touch screens or building anything you need. Everything that one needs to make Earth a paradise for all mankind is available by the grace of God.
Sunday, October 24, 2010
Friday, October 22, 2010
IEEE Theme Songs
The EE Bunch
Personally, I think Högt Över Havet is the best EE song ever written.
Högt Över Havet
Personally, I think Högt Över Havet is the best EE song ever written.
Högt Över Havet
STN Theme Song
Here is my latest idea for a theme song for STN. Change "Blue Hawaii" to "STN" in the Vikingarna song with other appropriate changes.
Till Mitt Eget STN
Nu reser jag till STN land = Now I travel to STN land
till varm och solig strand = a warm and sunny beach.
jag surfar över vågorna = I surf over the waves
som tar mej intill land = that take me in towards land,
där flickorna dom danser = where the girls are dancing
hula hula natten lång = hula hula the whole night long
i takt med vindens melodi = along with the wind's melody
sjunger vi en sång = we all sing along
i vårt eget STN = in our own STN
i vårt eget STN = in our own STN
vi vandrar tätt intill varann = We are walking close to each other
i kvällens solnedgång = in the evening's sunset
och ukulelen spelar upp = and ukulele playing
i vårt eget STN = in our own STN
i vårt eget STN = in our own STN
STN vårt eget STN = STN our own STN
hand i hand på en solig strand = hand in hand on a sunny beach
nu är jag här i STNs land = now I'm here in STN land
i mitt eget STN = in my own STN
Himmels egen sång = Heaven's own song!!!
©2010______________________________________________
Here are videos with the other version:
Till mitt eget blue hawaii
Metal Version
Anachronistic Version (from the late 80th century)
On Swedish Idol with English Subtitles
Line Dance
Cool Version
The German Language Version
Dance Band Version
one last one. There are hundreds more.
Till Mitt Eget STN
Nu reser jag till STN land = Now I travel to STN land
till varm och solig strand = a warm and sunny beach.
jag surfar över vågorna = I surf over the waves
som tar mej intill land = that take me in towards land,
där flickorna dom danser = where the girls are dancing
hula hula natten lång = hula hula the whole night long
i takt med vindens melodi = along with the wind's melody
sjunger vi en sång = we all sing along
i vårt eget STN = in our own STN
i vårt eget STN = in our own STN
vi vandrar tätt intill varann = We are walking close to each other
i kvällens solnedgång = in the evening's sunset
och ukulelen spelar upp = and ukulele playing
i vårt eget STN = in our own STN
i vårt eget STN = in our own STN
STN vårt eget STN = STN our own STN
hand i hand på en solig strand = hand in hand on a sunny beach
nu är jag här i STNs land = now I'm here in STN land
i mitt eget STN = in my own STN
Himmels egen sång = Heaven's own song!!!
©2010______________________________________________
Here are videos with the other version:
Till mitt eget blue hawaii
Metal Version
Anachronistic Version (from the late 80th century)
On Swedish Idol with English Subtitles
Line Dance
Cool Version
The German Language Version
Dance Band Version
one last one. There are hundreds more.
Thursday, October 21, 2010
Swedish Lession
This post is just exercise to say something in Swedish. Chitchat. Whatever comes to mind. Vardagsmat. Warning: I am just learning Swedish, so it will probably not make much sense.
Tjena! Jag heter Camery, den varmaste namn i den walesiska språket. Jag älskar när Katherine Jenkins, min favorit sångare, säger "Kom igen, Cymraeg!" Att få folk att sjunga om sin kärlek till gamla Cymry. Mitt namn är Kammerer på svenska och tyska. För länge sen, det var Camerer på latin. Dess etymologi är från platsen fortfarande kallas Cambria. Jag talar inte svenska, i alla fall ingen som vill höra min röst. När någon blockerar mig på Facebook, jag vill säga, "Snälla, gå inte förbi!", Men jag vet att de inte förstår svenska. Jag undrar ofta hur man säger det i engelska, mitt modersmål. Jag vet ingen sådan idiomatiskt uttryck på engelska för detta. Ändå vår tystnad säger åt dem att gå och kasta oss ut ur deras hjärtan.
The words must mean something different from what I feel in my soul.
According to Google, it translates into the following nonsense: Howdy! My name Camery, the hottest name in the Welsh language. I love when Katherine Jenkins, my favorite singers, saying "Come on, Cymraeg!" To get people to sing about his love for old Cymry. My name is Kammerer in Swedish and German. Long ago, it was Camere in Latin. Its etymology is from the site still known as Cambria. I do not speak Swedish, in all cases no one wants to hear my voice. When someone is blocking me on Facebook, I want to say, "Please, Do not bypass," But I know they do not understand Swedish. I often wonder how to say it in English, my native language. I know no such idiom in English for this. Yet our silence tells them to go and throw us out of their hearts.
Du kan inte säga att jag inte prova, men jag får några positiva resultat!
Tjena! Jag heter Camery, den varmaste namn i den walesiska språket. Jag älskar när Katherine Jenkins, min favorit sångare, säger "Kom igen, Cymraeg!" Att få folk att sjunga om sin kärlek till gamla Cymry. Mitt namn är Kammerer på svenska och tyska. För länge sen, det var Camerer på latin. Dess etymologi är från platsen fortfarande kallas Cambria. Jag talar inte svenska, i alla fall ingen som vill höra min röst. När någon blockerar mig på Facebook, jag vill säga, "Snälla, gå inte förbi!", Men jag vet att de inte förstår svenska. Jag undrar ofta hur man säger det i engelska, mitt modersmål. Jag vet ingen sådan idiomatiskt uttryck på engelska för detta. Ändå vår tystnad säger åt dem att gå och kasta oss ut ur deras hjärtan.
The words must mean something different from what I feel in my soul.
According to Google, it translates into the following nonsense: Howdy! My name Camery, the hottest name in the Welsh language. I love when Katherine Jenkins, my favorite singers, saying "Come on, Cymraeg!" To get people to sing about his love for old Cymry. My name is Kammerer in Swedish and German. Long ago, it was Camere in Latin. Its etymology is from the site still known as Cambria. I do not speak Swedish, in all cases no one wants to hear my voice. When someone is blocking me on Facebook, I want to say, "Please, Do not bypass," But I know they do not understand Swedish. I often wonder how to say it in English, my native language. I know no such idiom in English for this. Yet our silence tells them to go and throw us out of their hearts.
Du kan inte säga att jag inte prova, men jag får några positiva resultat!
Israeli Television Show
The New Season
Interview
The Theme Song
Another Song
Michael
Don't get sucked in!
On No! The Playlist.
Interview
The Theme Song
Another Song
Michael
Don't get sucked in!
On No! The Playlist.
Wednesday, October 20, 2010
Celebrating Passover
Probably, you didn't quite connect all the Biblical allusions in the whitepaper on Stuxnet or grasp why they are there. Maybe this will help.
The software project used to create the STUXNET was called guava. Guavas are plants in the myrtle (myrtus) family genus. The files it creates are called mrxcls.sys and mrxnet.sys. Myrtle branches were used to celebrate passover. First, we need some history.
Esther was originally named Hadassah. Hadassah means 'myrtle' in Hebrew." Esther learned of a plot to assassinate the king and "told the king of Haman's plan to massacre all Jews in the Persian Empire. Haman who set them up finally suffers for his crime of falsely implicating the jews by dying at the kings hands. The Jews went on to kill only their would-be executioners."
May 9, 1979 is the date the first Jew was executed by the Iranian government. It is also the day a Northwestern University graduate student was injured by a bomb made by the Unabomber. Earth is a dark and bloody planet.
When you type STUX in Hebrew you get דאוס (transcribed as Deus or DeOS). This happens to be the name of an Israeli children’s story playing on TV, where hackers develop a program named Deus which takes over the world.
Thus STUX is an allusion to God and 19790509 is an allusion to blood that you place on your door, i.e., in the registry of your computer, and the sacrifice that is required in order to avoid God’s wrath. Thus, we all must honor and celebrate Passover.
Actually, the current version of Stuxnet will only run on 32 bit versions of the following operating systems:
Win2K•
WinXP•
Windows 2003•
Vista•
Windows Server 2008•
Windows 7•
Windows Server 2008 R2•
If it is not running on one of these operating systems it will exit. So, I do not need to worry yet.
STUX is also known as Troj/Stuxnet-A [Sophos], W32/Stuxnet-B [Sophos], W32.Temphid [Symantec], WORM_STUXNET.A [Trend], Win32/Stuxnet.B [Computer Associates], Trojan-Dropper:W32/Stuxnet [F-Secure], Stuxnet [McAfee], W32/Stuxnet.A [Norman]
Decryption of the virus shows the following:
SOFTWARE\SIEMENS\WinCC\Setup
STEP7_Version
SOFTWARE\SIEMENS\STEP7
SOFTWARE\Microsoft\Windows\CurrentVersion\MS-DOS Emulation
NTVDM TRACE
The initial loader first checks that the configuration data is valid, after that it checks the value "NTVDM TRACE" in the following registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\MS-DOS Emulation
If this value is equal to 19790509 the threat will exit. This is thought to be an infection marker or a "do not infect" marker. If this is set correctly, infection will not occur.
Next, Stuxnet reads a date from the configuration data (offset 0x8c in the configuration data). If the current date is later than the date in the configuration file then infection will also not occur and the threat will exit. The date found in the current configuration file is June 24, 2012.
Alo, the registry is searched for indicators that the following anti-virus programs are installed:
KAV v6 to v9•
McAfee•
Trend PcCillin•
If one of the above security product processes are detected, version information of the main image is extracted. Based on the version number, the target process of injection will be determined or the injection process will fail if the virus considers the security product non-bypassable.
Discovered: July 13, 2010
Updated: September 17, 2010 8:53:13 AM
Also Known As: Troj/Stuxnet-A [Sophos], W32/Stuxnet-B [Sophos], W32.Temphid [Symantec], WORM_STUXNET.A [Trend], Win32/Stuxnet.B [Computer Associates], Trojan-Dropper:W32/Stuxnet [F-Secure], Stuxnet [McAfee], W32/Stuxnet.A [Norman]
Stuxnet was the first worm to exploit the Microsoft Windows Shortcut 'LNK/PIF' Files Automatic File Execution Vulnerability (BID 41732) in order to spread; in fact when Stuxnet was first discovered, this vulnerability was an unknown, or zero-day, vulnerability and it wasn’t until Stuxnet was analyzed that this vulnerability was recognized as such. Normally, when one thinks of a vulnerability in software, one would think of a coding error that an attacker discovers and then exploits. However, while this does indeed fit the definition of a vulnerability, specifically it is a design flaw as Windows is doing exactly what it was designed to do.
The virus copies itself to removable drives as the following files:
%DriveLetter%\~WTR4132.tmp
%DriveLetter%\~WTR4141.tmp
Note: Both file names are hardcoded and they are actually .dll files.
It also copies the following files to the above drives:
%DriveLetter%\Copy of Shortcut to.lnk
%DriveLetter%\Copy of Copy of Shortcut to.lnk
%DriveLetter%\Copy of Copy of Copy of Shortcut to.lnk
%DriveLetter%\Copy of Copy of Copy of Copy of Shortcut to.lnk
When the drive is accessed by an application that can display icons, such as Windows Explorer, instead of displaying the icon for the .lnk files, it runs code that executes the file %DriveLetter%\~WTR4132.tmp. This file’s main purpose is to execute the other file that is copied to the removable drive, DriveLetter%\~WTR4141.tmp, which is then loaded into memory. Its worth noting that this file has a valid signature issued to and signed by well-known companies in Taiwan.
It also uses a remote procedure call (RPC) exploit to spread. This exploit is only effective against computers that have not applied the patch for the Microsoft Windows Server Service RPC Handling Remote Code Execution Vulnerability (BID 31874).
Furthermore, it exploits the Microsoft Windows Print Spooler Service Remote Code Execution Vulnerability (BID 43073) to copy itself from one compromised computer to another. The vulnerability allows for a file to be written to the %System% directory of a vulnerable computer. Stuxnet first uses this vulnerability to plant a copy of itself on a vulnerable machine and later it uses a feature of WBEM to achieve execution of that file on the remote computer.
Stuxnet also attempts to spread via network shares by copying itself to network shares as the following file:
%DriveLetter%\ “DEFRAG[RANDOM NUMBER].tmp
Note: This file is in fact a .dll file.
It then attempts to create a job to run the .dll file.
The following file(s) may be seen on the compromised computer.
%System%\drivers\mrxcls.sys
%System%\drivers\mrxnet.sys
%DriveLetter%\~WTR4132.tmp
%DriveLetter%\~WTR4141.tmp
%DriveLetter%\Copy of Shortcut to.lnk
%DriveLetter%\Copy of Copy of Shortcut to.lnk
%DriveLetter%\Copy of Copy of Copy of Shortcut to.lnk
%DriveLetter%\Copy of Copy of Copy of Copy of Shortcut to.lnk
%Windir%\inf\oem6C.PNF
%Windir%\inf\oem7A.PNF
%Windir%\inf\mdmcpq3.PNF
%Windir%\inf\mdmeric3.PNF
The following registry entries are created:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\MRxCls\"ImagePath" = "%System%\drivers\mrxcls.sys"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\MRxNet\"ImagePath" = "%System%\drivers\mrxnet.sys"
It uses two processes:
iexplorer.exe (injection)
lsass.exe (injection)
Once an infected removable drive is attached to a clean computer, the virus copies itself to the clean computer as the following files:
%System%\drivers\mrxcls.sys
%System%\drivers\mrxnet.sys
Next, the virus registers the file mrxcls.sys as a service with the following characteristics:
Display Name: MRXCLS
Startup Type: Automatic
Image Path: %System%\drivers\mrxcls.sys
The virus creates the following registry entry for the above service:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\MRxCls\"ImagePath" = "%System%\drivers\mrxcls.sys"
It also registers the file mrxnet.sys as a service with the following characteristics:
Display Name: MRXNET
Startup Type: Automatic
Image Path: %System%\drivers\mrxnet.sys
The virus creates the following registry entry for the above service:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\MRxNet\"ImagePath" = "%System%\drivers\mrxnet.sys"
It also creates the following files, which are encrypted copies of the virus:
%Windir%\inf\oem6C.PNF
%Windir%\inf\oem7A.PNF
%Windir%\inf\mdmcpq3.PNF
%Windir%\inf\mdmeric3.PNF
The file %System%\drivers\mrxcls.sys decrypts these files to reinfect the compromised computer if attempts are made to remove the worm.
Downloading
The worm is able to download a payload executable on to the compromised computer from the C&C server and execute it.
The virus sends an HTTP request to the server containing information about the compromised computer. This information is sent by making a request to the following URL:
http://[C&C SERVER ADDRESS]/index.php?data=[DATA]
Note: DATA represents the system information that has been gathered.
The virus contacts the following URLs through port 80, which are the virus's Command and Control servers, to test Internet connectivity:
www.mypremierfutbol.com
www.todaysfutbol.com
The two URLs above were registered in Arizona and previously pointed to servers in Malaysia and Denmark. Names like this are typically American. “We don’t play soccer, we play futbol.” is a 21st century American expression.
The data is not sent in plain text though; instead it is encrypted with XOR using a 31-byte key. The data section also contains several fields describing the data. The response received back from the C&C server is also encrypted using XOR but using a different 31-byte key. Both of these keys are contained in the malicious .dll file on the compromised computer and can be used to decipher network traffic to and from the C&C server.
The data sent from the compromised computer to the C&C server contains the following information:
The Windows version information,
The computer name,
The network group name,
Flag for whether SCADA software was installed or not, and
IP addresses of all network interfaces.
When the C&C receives this information it can reply with 2 types of responses. The first type of response instructs the threat to execute one of the procedures already existing within the threats code. In fact the data from this type of response is forwarded to various RPC routines within the main .dll file. The second type of response delivers an additional .dll file to the client in the response and instructs the client to load that .dll file and call an ordinal one from within the downloaded .dll file.
The first type of response acts as a wrapper for RPCs that will be forwarded to the local machine. The RPC calls implemented on the client side can perform the following actions:
Read a file
Write to a file
Delete a file
Create a process
Inject a .dll into lsass.exe
Load an additional .dll file and executed export 1
Extract resource 210 from the main .dll file (this resource is used to inject into other processes)
Update the configuration data for the threat
The parameters for these RPC calls are passed to the client via response type 1. For example, the .dll file to be injected into lsass.exe is passed to the client from the server inside response type 1.
Stuxnet is specifically targeting systems with supervisory control and data acquisition (SCADA) software installed. The threat performs many database queries on the database used by the Siemens Step 7 software and interacts with the .dll files belonging to that product. It tries to extract specific data from the database. For example, it tries to access files with the following characteristics, created by the Step 7 software:
GracS\cc_tag.sav
GracS\cc_alg.sav
GracS\db_log.sav
GracS\cc_tlg7.sav
*.S7P
*.MCP
*.LDF
By accessing these files, Stuxnet steals code and design projects.
Industrial control systems consist of Programmable Logic Controllers (PLCs) that can be programmed from a Windows system. These PLCs contain special code that controls the automation of industrial processes. Programmers use software (e.g., on a Windows PC) to create code and then upload their code to the PLCs.
Stuxnet has the ability to take advantage of the programming software to also upload its own code to the PLC in an industrial control system that is typically monitored by SCADA systems. In addition, Stuxnet then hides these code blocks, so when a programmer using an infected machine tries to view all of the code blocks on a PLC, they will not see the code injected by Stuxnet. Thus, Stuxnet isn’t just a rootkit that hides itself on Windows, but is the first publicly known rootkit that is able to hide injected code located on a PLC.
In particular, Stuxnet hooks the programming software, which means that when someone uses the software to view code blocks on the PLC, the injected blocks are nowhere to be found. This is done by hooking enumeration, read, and write functions so that you can’t accidentally overwrite the hidden blocks as well. Thus Stuxnet introduces the first known rootkit for industrial control systems.
By writing code to the PLC, Stuxnet can potentially control or alter how the system operates. To date, no industrial facility has been knowingly compromised. What any attacker hopes to achieve by compromising an industrial facility is not known, but one thing is for sure: nothing good can come from a facility being compromised.
In an attempt to avoid detection the file %DriveLetter%\~WTR4132.tmp hides threat related files by hooking the following APIs from kernel32.dll and Ntdll.dll:
From Kernel32.dll
FindFirstFileW
FindNextFileW
FindFirstFileExW
From Ntdll.dll
NtQueryDirectoryFile
ZwQueryDirectoryFile
It replaces the original code for these functions with code that checks for files with the following properties:
File names ending with ".lnk"
File names beginning with "~WTR" and ending in ".tmp" (which explains why the file names on the removable drive are hardcoded and cannot change significantly)
If a request is made to list a file with the above properties, the response from these APIs is altered to state that the file does not exist, thereby hiding all files with those properties.
After the kernel32.dll APIs are hooked, the file %DriveLetter%\~WTR4132.tmp loads the other .dll file, %DriveLetter%\~WTR4141.tmp. However, to achieve this Stuxnet uses a different approach from what one would normally expect. Rather than calling the "LoadLibrary" API to load a .dll file into memory, which is what one would normally expect, Stuxnet hooks certain Ntdll.dll functions, then calls the “LoadLibrary” with a specially crafted file name. The file requested to be loaded does not exist on disk, therefore normally LoadLibrary would fail. However, W32.Stuxnet has hooked Ntdll.dll to monitor for requests to load specially crafted file names. If a specially crafted file name is encountered, the hooked ntdll.dll functions know to load a .dll file from another location instead; a location specified by Stuxnet and that location is generally an area in memory where a .dll file has been decrypted and stored by the threat previously.
The functions hooked for this purpose in Ntdll.dll are:
ZwMapViewOfSection
ZwCreateSection
ZwOpenFile
ZwCloseFile
ZwQueryAttributesFile
ZwQuerySection
Once a .dll file has been loaded, GetProcAddress is used to find the address of a specific export from the .dll file and that export is called, handing control to that new .dll file.
Stuxnet lower security settings and can inject its code into iexplorer.exe in order to bypass firewalls.
It also stops the following security-related processes:
vp.exe
Mcshield.exe
avguard.exe
bdagent.exe
UmxCfg.exe
fsdfwd.exe,
rtvscan.exe
ccSvcHst.exe
ekrn.exe
tmpproxy.exe
The vulnerability exploited by Stuxnet to escalate access privileges still exists.
STUXNET U.S.A., Israel, Taiwan, Denmark, Malaysia, Germany, etc.
Put 19790509 in the registry and it will passover you.
Sept 5, 2007 Air Defense in Syria neutralized.
November 20, 2008 Trojan.Zlob variant found to be using the LNK vulnerability only later identified in Stuxnet.
January, 2009 Compile date in virus.
June, 2009 Earliest Stuxnet sample seen.
July 5, 2009 Nuclear accident in Iran's Centrifuges
January 25, 2010 Stuxnet driver signed with a valid certificate belonging to Realtek Semiconductor Corps.
March, 2010 New Version exploits MS10-046, INSAT-4B???
June, 2010 Russian Disclosure
Stuxnet has even attacked Vanderlande's and Siemens' own systems.
September, 2010 "Iran has crossed the critical nuclear threshold taking it nearer to being able to arm ballistic missiles with nuclear warheads, weapons inspectors of the International Atomic Energy Agency reported last week.
October, 2010: The Fifth Fleet doubles combat power in the Persian Gulf. Forces mass near the border to attack Chad. Vengence is mine saith the LORD. Please save us from murdering ourselves.
What do the information assurance people say? They say people in information assurance are only allowed to talk to people in information assurance. They can hardly contain their laughter when someone foolishly tries to communicate with them.
In fact, Earth in the 21st Century is primary made up of cliques of people forbidden to have connections with each other. How odd? Maybe someone should check for aberrant methylation patterns in their cortex, liver and myometrium, if they have one. They do not seem human any more.
Who is there left to talk to? twitter, maybe, God surely.
The software project used to create the STUXNET was called guava. Guavas are plants in the myrtle (myrtus) family genus. The files it creates are called mrxcls.sys and mrxnet.sys. Myrtle branches were used to celebrate passover. First, we need some history.
Esther was originally named Hadassah. Hadassah means 'myrtle' in Hebrew." Esther learned of a plot to assassinate the king and "told the king of Haman's plan to massacre all Jews in the Persian Empire. Haman who set them up finally suffers for his crime of falsely implicating the jews by dying at the kings hands. The Jews went on to kill only their would-be executioners."
May 9, 1979 is the date the first Jew was executed by the Iranian government. It is also the day a Northwestern University graduate student was injured by a bomb made by the Unabomber. Earth is a dark and bloody planet.
When you type STUX in Hebrew you get דאוס (transcribed as Deus or DeOS). This happens to be the name of an Israeli children’s story playing on TV, where hackers develop a program named Deus which takes over the world.
Thus STUX is an allusion to God and 19790509 is an allusion to blood that you place on your door, i.e., in the registry of your computer, and the sacrifice that is required in order to avoid God’s wrath. Thus, we all must honor and celebrate Passover.
Actually, the current version of Stuxnet will only run on 32 bit versions of the following operating systems:
Win2K•
WinXP•
Windows 2003•
Vista•
Windows Server 2008•
Windows 7•
Windows Server 2008 R2•
If it is not running on one of these operating systems it will exit. So, I do not need to worry yet.
STUX is also known as Troj/Stuxnet-A [Sophos], W32/Stuxnet-B [Sophos], W32.Temphid [Symantec], WORM_STUXNET.A [Trend], Win32/Stuxnet.B [Computer Associates], Trojan-Dropper:W32/Stuxnet [F-Secure], Stuxnet [McAfee], W32/Stuxnet.A [Norman]
Decryption of the virus shows the following:
SOFTWARE\SIEMENS\WinCC\Setup
STEP7_Version
SOFTWARE\SIEMENS\STEP7
SOFTWARE\Microsoft\Windows\CurrentVersion\MS-DOS Emulation
NTVDM TRACE
The initial loader first checks that the configuration data is valid, after that it checks the value "NTVDM TRACE" in the following registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\MS-DOS Emulation
If this value is equal to 19790509 the threat will exit. This is thought to be an infection marker or a "do not infect" marker. If this is set correctly, infection will not occur.
Next, Stuxnet reads a date from the configuration data (offset 0x8c in the configuration data). If the current date is later than the date in the configuration file then infection will also not occur and the threat will exit. The date found in the current configuration file is June 24, 2012.
Alo, the registry is searched for indicators that the following anti-virus programs are installed:
KAV v6 to v9•
McAfee•
Trend PcCillin•
If one of the above security product processes are detected, version information of the main image is extracted. Based on the version number, the target process of injection will be determined or the injection process will fail if the virus considers the security product non-bypassable.
Discovered: July 13, 2010
Updated: September 17, 2010 8:53:13 AM
Also Known As: Troj/Stuxnet-A [Sophos], W32/Stuxnet-B [Sophos], W32.Temphid [Symantec], WORM_STUXNET.A [Trend], Win32/Stuxnet.B [Computer Associates], Trojan-Dropper:W32/Stuxnet [F-Secure], Stuxnet [McAfee], W32/Stuxnet.A [Norman]
Stuxnet was the first worm to exploit the Microsoft Windows Shortcut 'LNK/PIF' Files Automatic File Execution Vulnerability (BID 41732) in order to spread; in fact when Stuxnet was first discovered, this vulnerability was an unknown, or zero-day, vulnerability and it wasn’t until Stuxnet was analyzed that this vulnerability was recognized as such. Normally, when one thinks of a vulnerability in software, one would think of a coding error that an attacker discovers and then exploits. However, while this does indeed fit the definition of a vulnerability, specifically it is a design flaw as Windows is doing exactly what it was designed to do.
The virus copies itself to removable drives as the following files:
%DriveLetter%\~WTR4132.tmp
%DriveLetter%\~WTR4141.tmp
Note: Both file names are hardcoded and they are actually .dll files.
It also copies the following files to the above drives:
%DriveLetter%\Copy of Shortcut to.lnk
%DriveLetter%\Copy of Copy of Shortcut to.lnk
%DriveLetter%\Copy of Copy of Copy of Shortcut to.lnk
%DriveLetter%\Copy of Copy of Copy of Copy of Shortcut to.lnk
When the drive is accessed by an application that can display icons, such as Windows Explorer, instead of displaying the icon for the .lnk files, it runs code that executes the file %DriveLetter%\~WTR4132.tmp. This file’s main purpose is to execute the other file that is copied to the removable drive, DriveLetter%\~WTR4141.tmp, which is then loaded into memory. Its worth noting that this file has a valid signature issued to and signed by well-known companies in Taiwan.
It also uses a remote procedure call (RPC) exploit to spread. This exploit is only effective against computers that have not applied the patch for the Microsoft Windows Server Service RPC Handling Remote Code Execution Vulnerability (BID 31874).
Furthermore, it exploits the Microsoft Windows Print Spooler Service Remote Code Execution Vulnerability (BID 43073) to copy itself from one compromised computer to another. The vulnerability allows for a file to be written to the %System% directory of a vulnerable computer. Stuxnet first uses this vulnerability to plant a copy of itself on a vulnerable machine and later it uses a feature of WBEM to achieve execution of that file on the remote computer.
Stuxnet also attempts to spread via network shares by copying itself to network shares as the following file:
%DriveLetter%\ “DEFRAG[RANDOM NUMBER].tmp
Note: This file is in fact a .dll file.
It then attempts to create a job to run the .dll file.
The following file(s) may be seen on the compromised computer.
%System%\drivers\mrxcls.sys
%System%\drivers\mrxnet.sys
%DriveLetter%\~WTR4132.tmp
%DriveLetter%\~WTR4141.tmp
%DriveLetter%\Copy of Shortcut to.lnk
%DriveLetter%\Copy of Copy of Shortcut to.lnk
%DriveLetter%\Copy of Copy of Copy of Shortcut to.lnk
%DriveLetter%\Copy of Copy of Copy of Copy of Shortcut to.lnk
%Windir%\inf\oem6C.PNF
%Windir%\inf\oem7A.PNF
%Windir%\inf\mdmcpq3.PNF
%Windir%\inf\mdmeric3.PNF
The following registry entries are created:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\MRxCls\"ImagePath" = "%System%\drivers\mrxcls.sys"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\MRxNet\"ImagePath" = "%System%\drivers\mrxnet.sys"
It uses two processes:
iexplorer.exe (injection)
lsass.exe (injection)
Once an infected removable drive is attached to a clean computer, the virus copies itself to the clean computer as the following files:
%System%\drivers\mrxcls.sys
%System%\drivers\mrxnet.sys
Next, the virus registers the file mrxcls.sys as a service with the following characteristics:
Display Name: MRXCLS
Startup Type: Automatic
Image Path: %System%\drivers\mrxcls.sys
The virus creates the following registry entry for the above service:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\MRxCls\"ImagePath" = "%System%\drivers\mrxcls.sys"
It also registers the file mrxnet.sys as a service with the following characteristics:
Display Name: MRXNET
Startup Type: Automatic
Image Path: %System%\drivers\mrxnet.sys
The virus creates the following registry entry for the above service:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\MRxNet\"ImagePath" = "%System%\drivers\mrxnet.sys"
It also creates the following files, which are encrypted copies of the virus:
%Windir%\inf\oem6C.PNF
%Windir%\inf\oem7A.PNF
%Windir%\inf\mdmcpq3.PNF
%Windir%\inf\mdmeric3.PNF
The file %System%\drivers\mrxcls.sys decrypts these files to reinfect the compromised computer if attempts are made to remove the worm.
Downloading
The worm is able to download a payload executable on to the compromised computer from the C&C server and execute it.
The virus sends an HTTP request to the server containing information about the compromised computer. This information is sent by making a request to the following URL:
http://[C&C SERVER ADDRESS]/index.php?data=[DATA]
Note: DATA represents the system information that has been gathered.
The virus contacts the following URLs through port 80, which are the virus's Command and Control servers, to test Internet connectivity:
www.mypremierfutbol.com
www.todaysfutbol.com
The two URLs above were registered in Arizona and previously pointed to servers in Malaysia and Denmark. Names like this are typically American. “We don’t play soccer, we play futbol.” is a 21st century American expression.
The data is not sent in plain text though; instead it is encrypted with XOR using a 31-byte key. The data section also contains several fields describing the data. The response received back from the C&C server is also encrypted using XOR but using a different 31-byte key. Both of these keys are contained in the malicious .dll file on the compromised computer and can be used to decipher network traffic to and from the C&C server.
The data sent from the compromised computer to the C&C server contains the following information:
The Windows version information,
The computer name,
The network group name,
Flag for whether SCADA software was installed or not, and
IP addresses of all network interfaces.
When the C&C receives this information it can reply with 2 types of responses. The first type of response instructs the threat to execute one of the procedures already existing within the threats code. In fact the data from this type of response is forwarded to various RPC routines within the main .dll file. The second type of response delivers an additional .dll file to the client in the response and instructs the client to load that .dll file and call an ordinal one from within the downloaded .dll file.
The first type of response acts as a wrapper for RPCs that will be forwarded to the local machine. The RPC calls implemented on the client side can perform the following actions:
Read a file
Write to a file
Delete a file
Create a process
Inject a .dll into lsass.exe
Load an additional .dll file and executed export 1
Extract resource 210 from the main .dll file (this resource is used to inject into other processes)
Update the configuration data for the threat
The parameters for these RPC calls are passed to the client via response type 1. For example, the .dll file to be injected into lsass.exe is passed to the client from the server inside response type 1.
Stuxnet is specifically targeting systems with supervisory control and data acquisition (SCADA) software installed. The threat performs many database queries on the database used by the Siemens Step 7 software and interacts with the .dll files belonging to that product. It tries to extract specific data from the database. For example, it tries to access files with the following characteristics, created by the Step 7 software:
GracS\cc_tag.sav
GracS\cc_alg.sav
GracS\db_log.sav
GracS\cc_tlg7.sav
*.S7P
*.MCP
*.LDF
By accessing these files, Stuxnet steals code and design projects.
Industrial control systems consist of Programmable Logic Controllers (PLCs) that can be programmed from a Windows system. These PLCs contain special code that controls the automation of industrial processes. Programmers use software (e.g., on a Windows PC) to create code and then upload their code to the PLCs.
Stuxnet has the ability to take advantage of the programming software to also upload its own code to the PLC in an industrial control system that is typically monitored by SCADA systems. In addition, Stuxnet then hides these code blocks, so when a programmer using an infected machine tries to view all of the code blocks on a PLC, they will not see the code injected by Stuxnet. Thus, Stuxnet isn’t just a rootkit that hides itself on Windows, but is the first publicly known rootkit that is able to hide injected code located on a PLC.
In particular, Stuxnet hooks the programming software, which means that when someone uses the software to view code blocks on the PLC, the injected blocks are nowhere to be found. This is done by hooking enumeration, read, and write functions so that you can’t accidentally overwrite the hidden blocks as well. Thus Stuxnet introduces the first known rootkit for industrial control systems.
By writing code to the PLC, Stuxnet can potentially control or alter how the system operates. To date, no industrial facility has been knowingly compromised. What any attacker hopes to achieve by compromising an industrial facility is not known, but one thing is for sure: nothing good can come from a facility being compromised.
In an attempt to avoid detection the file %DriveLetter%\~WTR4132.tmp hides threat related files by hooking the following APIs from kernel32.dll and Ntdll.dll:
From Kernel32.dll
FindFirstFileW
FindNextFileW
FindFirstFileExW
From Ntdll.dll
NtQueryDirectoryFile
ZwQueryDirectoryFile
It replaces the original code for these functions with code that checks for files with the following properties:
File names ending with ".lnk"
File names beginning with "~WTR" and ending in ".tmp" (which explains why the file names on the removable drive are hardcoded and cannot change significantly)
If a request is made to list a file with the above properties, the response from these APIs is altered to state that the file does not exist, thereby hiding all files with those properties.
After the kernel32.dll APIs are hooked, the file %DriveLetter%\~WTR4132.tmp loads the other .dll file, %DriveLetter%\~WTR4141.tmp. However, to achieve this Stuxnet uses a different approach from what one would normally expect. Rather than calling the "LoadLibrary" API to load a .dll file into memory, which is what one would normally expect, Stuxnet hooks certain Ntdll.dll functions, then calls the “LoadLibrary” with a specially crafted file name. The file requested to be loaded does not exist on disk, therefore normally LoadLibrary would fail. However, W32.Stuxnet has hooked Ntdll.dll to monitor for requests to load specially crafted file names. If a specially crafted file name is encountered, the hooked ntdll.dll functions know to load a .dll file from another location instead; a location specified by Stuxnet and that location is generally an area in memory where a .dll file has been decrypted and stored by the threat previously.
The functions hooked for this purpose in Ntdll.dll are:
ZwMapViewOfSection
ZwCreateSection
ZwOpenFile
ZwCloseFile
ZwQueryAttributesFile
ZwQuerySection
Once a .dll file has been loaded, GetProcAddress is used to find the address of a specific export from the .dll file and that export is called, handing control to that new .dll file.
Stuxnet lower security settings and can inject its code into iexplorer.exe in order to bypass firewalls.
It also stops the following security-related processes:
vp.exe
Mcshield.exe
avguard.exe
bdagent.exe
UmxCfg.exe
fsdfwd.exe,
rtvscan.exe
ccSvcHst.exe
ekrn.exe
tmpproxy.exe
The vulnerability exploited by Stuxnet to escalate access privileges still exists.
STUXNET U.S.A., Israel, Taiwan, Denmark, Malaysia, Germany, etc.
Put 19790509 in the registry and it will passover you.
Sept 5, 2007 Air Defense in Syria neutralized.
November 20, 2008 Trojan.Zlob variant found to be using the LNK vulnerability only later identified in Stuxnet.
January, 2009 Compile date in virus.
June, 2009 Earliest Stuxnet sample seen.
July 5, 2009 Nuclear accident in Iran's Centrifuges
January 25, 2010 Stuxnet driver signed with a valid certificate belonging to Realtek Semiconductor Corps.
March, 2010 New Version exploits MS10-046, INSAT-4B???
June, 2010 Russian Disclosure
Stuxnet has even attacked Vanderlande's and Siemens' own systems.
September, 2010 "Iran has crossed the critical nuclear threshold taking it nearer to being able to arm ballistic missiles with nuclear warheads, weapons inspectors of the International Atomic Energy Agency reported last week.
October, 2010: The Fifth Fleet doubles combat power in the Persian Gulf. Forces mass near the border to attack Chad. Vengence is mine saith the LORD. Please save us from murdering ourselves.
What do the information assurance people say? They say people in information assurance are only allowed to talk to people in information assurance. They can hardly contain their laughter when someone foolishly tries to communicate with them.
In fact, Earth in the 21st Century is primary made up of cliques of people forbidden to have connections with each other. How odd? Maybe someone should check for aberrant methylation patterns in their cortex, liver and myometrium, if they have one. They do not seem human any more.
Who is there left to talk to? twitter, maybe, God surely.
Tuesday, October 19, 2010
Since when did Murky Death become Cut-Throat?

Conversation with a Swede:
Swede: I find this hilarious. Because the fact that I’m a Swede, I can make this into a double joke.
"Killing" means, well, killing, in English. But in Swedish "Killar" means tickling. so if you want to say that you are both tickling and killing "me", you can say killing me XD
....
Oh well, its funnier if you’re a Swede.
Non-Swede: Cool...Does Killar mean 'killing' and 'tickling' then?
Swede: noooot really..
Killar = Guys AND tickling
Non-Swede: Oh! I see.
Now look deeper!
Suppose one says:
Hej, stark killar!
This should sound like a complement. If it does not, you are probably suffering from the paranoid influence of Arabic: قاتل (qātel). The English word is murder: From Middle English murder, murdre, mourdre "murder", alteration of earlier murthre "murder" (See murther) from Old English morþor "dark death" and Old English myrþra "murder, homicide", Akin to Gothic (maurþr) "murder"and Swedish mördar, Old High German mord "murder", Old Norse morð "murder", Old English myrþrian "to murder".
The -d- in the Middle English form may have been influenced in part by Anglo-Norman murdre from Medieval Latin murdrum from Old French murdre from Frankish *murþra "murder", from the same Germanic root, though this may also have wholly been the result of internal development. Personally, I always see the roots as "Murky Death" in all these languages.
The idea that there should be a word, such as, killer, cut-throat, etc. in civilized language would be repugnant to the sensibilities of our ancestors. What have we come to?
Only Arabs, etc. should talk of killing. It is their word. We are not paranoid.
Friday, October 15, 2010
Religious Psychology
Do you perceive God as an eternal repetitive force throughout time or a real living force existing at a place and time?
Do you see life as a struggle against the devil or a love affair with God?
Do you hate your enemies or love them?
Do you hate the weak and defenseless or do you want to help them?
Do you belong to a superstitious cult bent on imposing it’s rituals on others or do you serve God?
Do you believe in predestination or do you believe that your choices can make the world a better place?
Excitrons in Graphene exhibit time reversal symmetry allowing one to calculate the percentage of photons they absorb. Does this make Graphene transparent or visible?
In other words, are you a paranoid schizophrenic who wants to kill me or a happy normal person?
Do you see life as a struggle against the devil or a love affair with God?
Do you hate your enemies or love them?
Do you hate the weak and defenseless or do you want to help them?
Do you belong to a superstitious cult bent on imposing it’s rituals on others or do you serve God?
Do you believe in predestination or do you believe that your choices can make the world a better place?
Excitrons in Graphene exhibit time reversal symmetry allowing one to calculate the percentage of photons they absorb. Does this make Graphene transparent or visible?
In other words, are you a paranoid schizophrenic who wants to kill me or a happy normal person?
Wednesday, October 13, 2010
Tuesday, October 12, 2010
Words used to denote God.
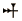 is a phonetic sign denoting the syllable "an". Note that it is a cross making it easy to remember what it stands for. It also stands for three logograms: the word ilum which means "god" (but transliterated as DINGIR, the Sumerian word for "god"), the god of heaven Anum, and then by extension the word šamû which means "heaven". And on top of all this, it can also function as a determinative for names of deities. The following example illustrates this polyvalency:
is a phonetic sign denoting the syllable "an". Note that it is a cross making it easy to remember what it stands for. It also stands for three logograms: the word ilum which means "god" (but transliterated as DINGIR, the Sumerian word for "god"), the god of heaven Anum, and then by extension the word šamû which means "heaven". And on top of all this, it can also function as a determinative for names of deities. The following example illustrates this polyvalency:
I remember the Sumerian word by thinking of the Egyptian hieroglyph, representing the d sound which is pictured as a hand which reminds me of fingers which is about as close as you can get to DINGIR in English and as a bonus it reminds me of the phonetic sound “an” and the determinative, D. I cheat and use Egyptian as mnemonic aids instead of Latin grammar like you are supposed to when learning, Gothic, Swedish, etc.
It seems to me that most all of the words for God derive from Sumerian / Akkadian where the determinative for deity name is "D". In recent times, certain pronunciations have come to represent the imperative of agape while others convey the opposite, viz. jihad.
The term in English is God, in Swedish: Gud, in French: Dieu, in Italian: Dio, in German: Gott, in Yiddish: Got, in Spanish: Dios, in Portuguese: Deus, in Greek: Theos, in Gothic: Guþ, in Arabic: al-dhat and الله, in Hebrew: El, in Aramaic: El, etc.
Quick note on the traditional transliteration of Akkadian signs: Phonograms are written in italic. Logograms are written in capitals, often transcribing Sumerian words, but also sometimes Akkadian if the logogram has more meanings in Akkadian than in Sumerian. The superscripts are determinatives, and they tend to use the same convention as logograms (capital letters transcribing Sumerian words). The only exception is the determinative for deity names, which is shortened to D instead of DINGIR.
Going back to the example, you have most likely noticed that the same sign can represent different words. This polyvalency originated in Sumerian when the same logogram was used to write related words that had vastly different pronunciations. To distinguish between different readings, contextual information is extremely important. One kind of hint to indicate which word the logogram refers is the phonetic complement. It is a phonogram that spells out part of the word that the logogram represents, and so allow the reader to identify the word. In the example, the sign sequence AN-ú identifies the word šamû, not the deity Anum. Another form of hint is the determinative. The sequence KÁ-DINGIR-RA is followed by the determinative KI, meaning that is must be the name of a city. Only one city is written as KÁ-DINGIR-RA, and that would be Babylon. In fact, the logogram KÁ represents the word babu ("gate"), DINGIR resolves to ilum ("god"), and RA is the genitive case in Sumerian for dingir. Together the sequence gives Babilum, or "Gate of the God", where the god in question would be Marduk, the patron god of Babylon.
See how simple the language of these Earthings is!!!
Wednesday, October 6, 2010
Vision av en ny fysik
Jag ser mig omkring och allt jag ser är kvanta med diskreta energinivåer i en rumtid omvandla deras spinn, dalar, laddning, rörelsemängd när jag ser. Inte en enda kvark. Ingen tid, bara rumtiden. Ingen massa bortsett från kvantiserad energi i rumtiden. Nej magnetism, bara elektrosvag kraft i rumtiden. Nej Fermioner, bara ett slags utanförskap princip långt ifrån grundläggande. Kvarkar, tid, magnetism ... är alla illusioner. De är bara oskiljaktiga delar av en större helhet. Inte konstigt att jag älskar BEC!
The above is just my practise for today writing in Swedish. Below is a wordlist I found.
Här följer en ordlista som förhoppningsvis förtydligar vissa abstrakta och krångliga begrepp:
•Egentid: Är den tid som varje observatör upplever. Denna betecknas och är fundamental vid räknandet med 4-vektorer för partikeln eftersom endast dess egen tid är referensramoberoende.
•Eter: Medium som behövs för att mekaniska signaler skall kunna fortplantas.
•Gammafaktorn: Olinjär funktion som ger hur mycket ett observerat objekt förändras med begreppen längd, massa och tid vid den relativa hastigheten v. Funktionen för gammafaktorn har en lodrät asymptot vid hastigheten c - ljushastigheten - och är nedåt begränsad till ett.
•Inertialram: Kallas det koordinatsystem som befinner sig i vila relativt en viss observatör. För samtliga inertialramar gäller att fysikens lagar är identiska för alla objekt som befinner sig i vila relativt dem.
•Invariant: Avståndet mellan två händelser i rumtiden är oberoende av valet av koordinatsystem.
•Isotrop: Betyder att någonting är likadant i alla riktningar.
•Koherent: Betyder att någonting är i fas. Gäller det ljusvågor så innebär detta att de förstärker varandra.
•Kontravarians: Bevaras ej vid en transformation(?). 1-former är kontravarianta inom teorin för differentialformer. Har indexet upphöjt.
•Kovarians: Bevaras vid en transformation(?). Vektorer är kovarianta inom teorin för differentialformer. Har indexet nedsänkt.
•Kovariant derivata: En generalisering av begreppet partiell derivata som kompenserar för rummets krökning.
•Lorentzram: Annat ord för inertialram.
•Machs princip: En kropp i ett universum utan andra massor har ingen rörelsemängd.
•Observatör: Fiktivt objekt som befinner sig i en lokal inertialram och som kan studera omgivningen utan att påverka den genom att ha väldigt liten massa.
•Olinjär: Innebär att något inte är linjärt, d v s kan inte beskrivas överallt med raka linjer mer än ungefärligt i enstaka punkter.
•Perihelium: Den punkt i en himlakropps elliptiska bana runt stjärnan där himlakroppen är som närmast stjärnan.
•Postulat: Grundläggande konstateranden som kan sägas motsvaras av axiom inom matematiken.
•Pseudoparadox: Fenomen som verkar vara en paradox men som vid en grundlig undersökning i själva verket inte är det.
•Rumtid: Abstraherande av tiden till en fjärde dimension. Därefter räknar man som om rummet består av fyra dimensioner och får därmed möjligheten att bestämma händelser i rumtiden unikt.
•Tankeexperiment: Fiktivt experiment, förknippat med Albert Einstein, som oftast är så extremt att det är omöjligt att genomföra i verkligheten men som hjälper till att komma vidare med utvecklandet och förståelsen av en teori.
•Transformation: Matematisk operation som genom en funktion överför en uppsättning tillstånd till en annan uppsättning tillstånd.
The above is just my practise for today writing in Swedish. Below is a wordlist I found.
Här följer en ordlista som förhoppningsvis förtydligar vissa abstrakta och krångliga begrepp:
•Egentid: Är den tid som varje observatör upplever. Denna betecknas och är fundamental vid räknandet med 4-vektorer för partikeln eftersom endast dess egen tid är referensramoberoende.
•Eter: Medium som behövs för att mekaniska signaler skall kunna fortplantas.
•Gammafaktorn: Olinjär funktion som ger hur mycket ett observerat objekt förändras med begreppen längd, massa och tid vid den relativa hastigheten v. Funktionen för gammafaktorn har en lodrät asymptot vid hastigheten c - ljushastigheten - och är nedåt begränsad till ett.
•Inertialram: Kallas det koordinatsystem som befinner sig i vila relativt en viss observatör. För samtliga inertialramar gäller att fysikens lagar är identiska för alla objekt som befinner sig i vila relativt dem.
•Invariant: Avståndet mellan två händelser i rumtiden är oberoende av valet av koordinatsystem.
•Isotrop: Betyder att någonting är likadant i alla riktningar.
•Koherent: Betyder att någonting är i fas. Gäller det ljusvågor så innebär detta att de förstärker varandra.
•Kontravarians: Bevaras ej vid en transformation(?). 1-former är kontravarianta inom teorin för differentialformer. Har indexet upphöjt.
•Kovarians: Bevaras vid en transformation(?). Vektorer är kovarianta inom teorin för differentialformer. Har indexet nedsänkt.
•Kovariant derivata: En generalisering av begreppet partiell derivata som kompenserar för rummets krökning.
•Lorentzram: Annat ord för inertialram.
•Machs princip: En kropp i ett universum utan andra massor har ingen rörelsemängd.
•Observatör: Fiktivt objekt som befinner sig i en lokal inertialram och som kan studera omgivningen utan att påverka den genom att ha väldigt liten massa.
•Olinjär: Innebär att något inte är linjärt, d v s kan inte beskrivas överallt med raka linjer mer än ungefärligt i enstaka punkter.
•Perihelium: Den punkt i en himlakropps elliptiska bana runt stjärnan där himlakroppen är som närmast stjärnan.
•Postulat: Grundläggande konstateranden som kan sägas motsvaras av axiom inom matematiken.
•Pseudoparadox: Fenomen som verkar vara en paradox men som vid en grundlig undersökning i själva verket inte är det.
•Rumtid: Abstraherande av tiden till en fjärde dimension. Därefter räknar man som om rummet består av fyra dimensioner och får därmed möjligheten att bestämma händelser i rumtiden unikt.
•Tankeexperiment: Fiktivt experiment, förknippat med Albert Einstein, som oftast är så extremt att det är omöjligt att genomföra i verkligheten men som hjälper till att komma vidare med utvecklandet och förståelsen av en teori.
•Transformation: Matematisk operation som genom en funktion överför en uppsättning tillstånd till en annan uppsättning tillstånd.
Subscribe to:
Posts (Atom)


